Understanding PKCE: Enhancing OAuth 2.0 Security
In the ever-evolving landscape of web security, the need for robust authentication methods has never been greater. One protocol gaining traction in securing APIs and user data is the Proof Key for Code Exchange (PKCE), an extension of the OAuth 2.0 framework. Let’s delve into what PKCE is and why it’s essential for modern applications.
What is PKCE?
PKCE (pronounced “pixy”) was originally designed to improve the security of OAuth 2.0, particularly for mobile and public clients that cannot securely store secrets. The protocol mitigates the risk of authorization code interception attacks, where malicious actors might capture the authorization code during the authentication flow.
How PKCE Works
PKCE enhances the OAuth 2.0 authorization code flow through two key components:
- Code Verifier: A cryptographically random string generated by the client before initiating the authorization request.
- Code Challenge: A hashed version of the code verifier, sent along with the authorization request to the authorization server.
The flow operates as follows:
- The client generates a code verifier and derives the code challenge from it.
- The client initiates the OAuth flow, including the code challenge in the request.
- The user authenticates and is redirected back to the client with an authorization code.
- The client then sends the authorization code along with the original code verifier to the token endpoint.
- The server validates the code challenge against the code verifier. If they match, it issues an access token.
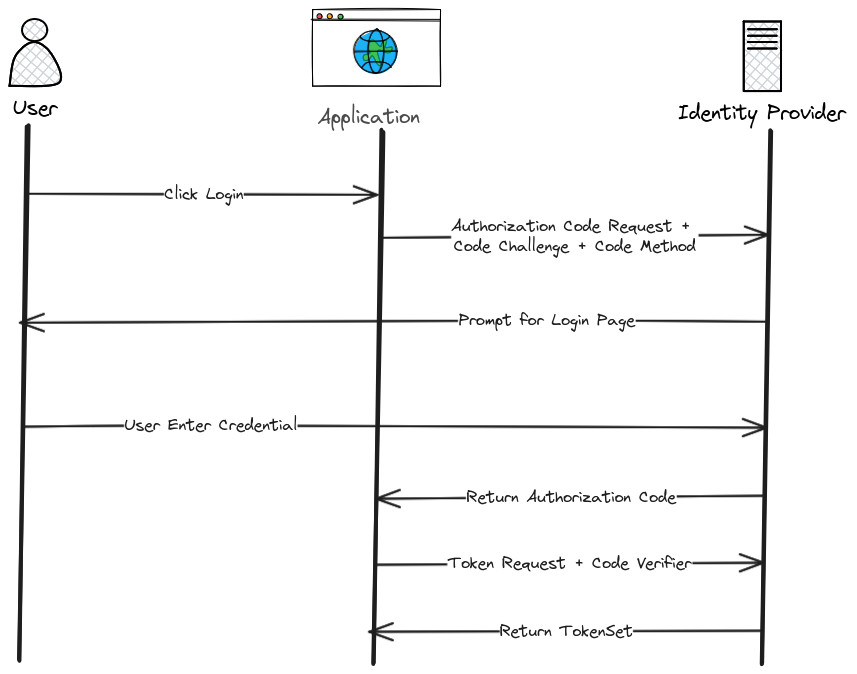
This mechanism ensures that even if an attacker captures the authorization code, they cannot exchange it for an access token without the original code verifier.
How PKCE Increases Security
-
Protection Against Authorization Code Interception:
- In traditional OAuth 2.0 flows, if an attacker intercepts the authorization code during the redirection process, they can use it to obtain an access token. PKCE mitigates this risk by requiring the client to present a code verifier that is known only to it. Without this code verifier, even if the attacker has the authorization code, they cannot exchange it for an access token.
-
Dynamic Challenge-Response Mechanism:
- PKCE introduces a challenge-response mechanism through the code challenge and code verifier. The code challenge (a hashed version of the code verifier) is sent to the authorization server, while the actual code verifier is kept secret by the client. This means that each authorization request involves a unique code verifier and code challenge, making replay attacks much more difficult.
-
No Client Secrets Required:
- PKCE is particularly beneficial for public clients (like mobile or single-page applications) that cannot securely store client secrets. Since these types of clients often face a higher risk of code interception, PKCE provides a way to authenticate users without needing to store sensitive information, thus reducing potential attack vectors.
-
Mitigating Phishing Attacks:
- In cases where users might be tricked into entering their credentials on a malicious site, PKCE ensures that only the legitimate client can exchange the authorization code for tokens. The attacker may obtain the authorization code, but without the correct code verifier, they cannot access the tokens.
-
Increased Trust with Authorization Server:
- Since the server must validate the code challenge against the provided code verifier, it reinforces the trust relationship between the client and the server. This validation step ensures that only authorized clients can complete the authentication flow, adding an additional layer of security.
Conclusion
As cybersecurity threats continue to evolve, implementing robust authentication protocols is crucial. PKCE provides a significant security upgrade to OAuth 2.0, especially for mobile and public applications. By leveraging PKCE, developers can help safeguard user data and maintain the integrity of their applications in an increasingly complex digital world. Embracing this protocol is not just a best practice—it’s a necessity for building secure applications today.
